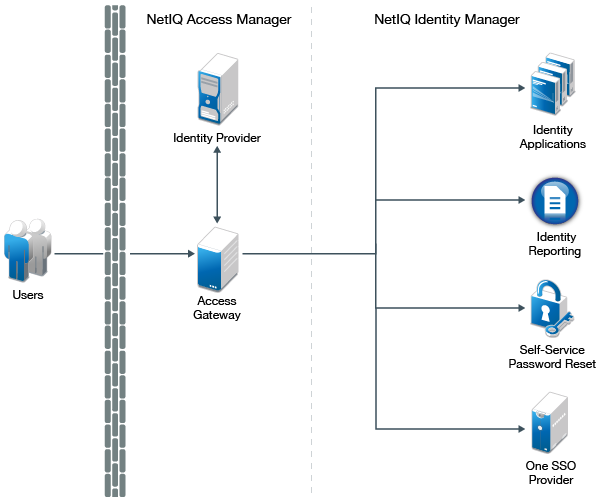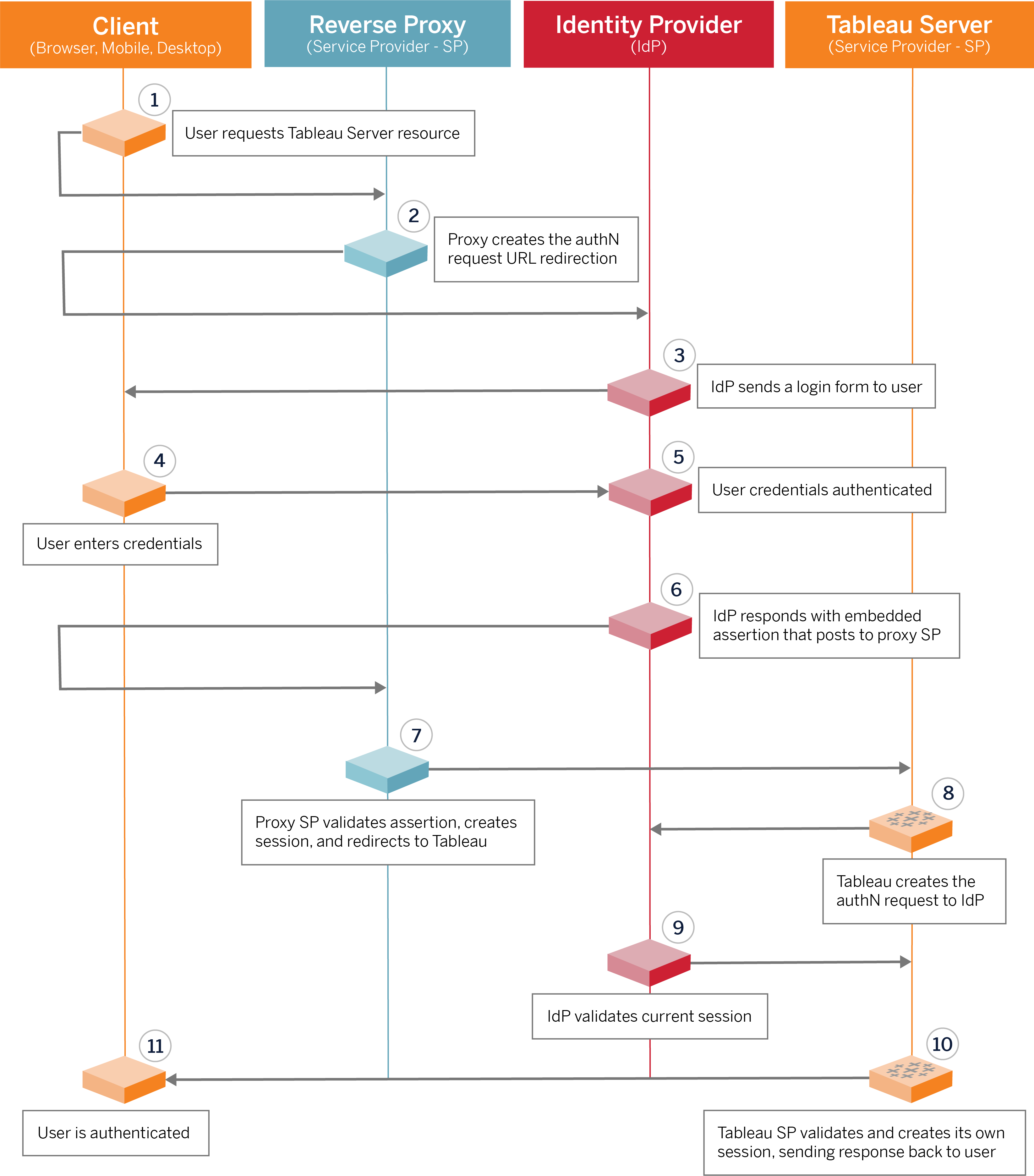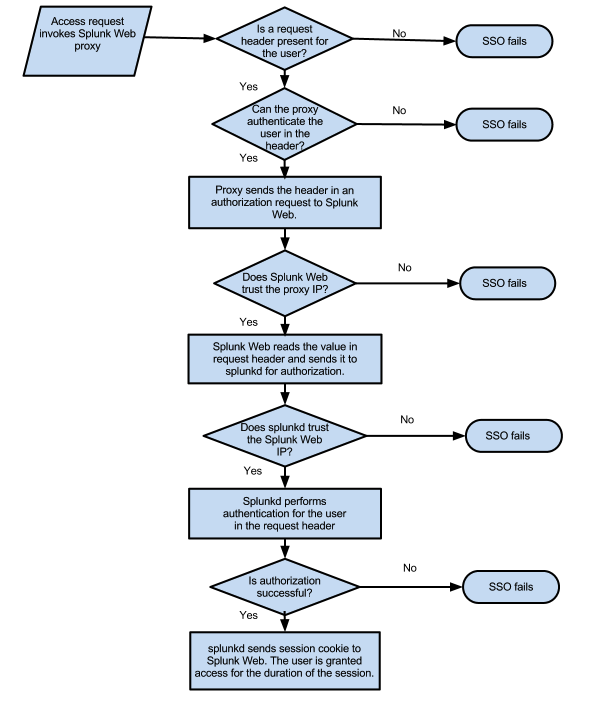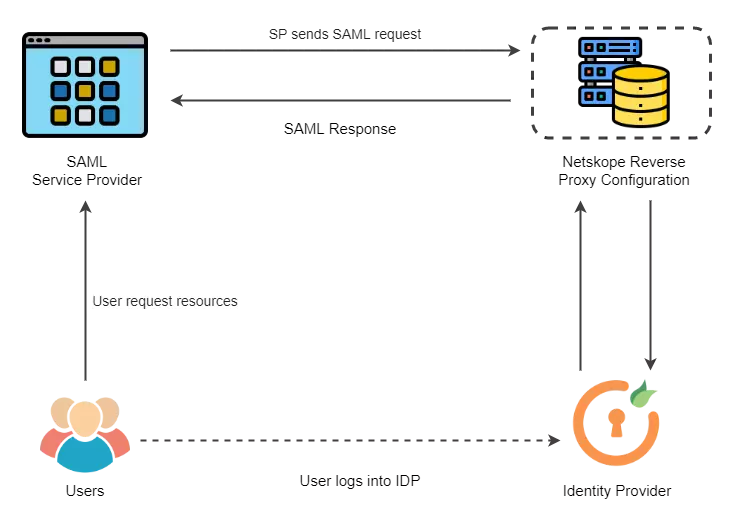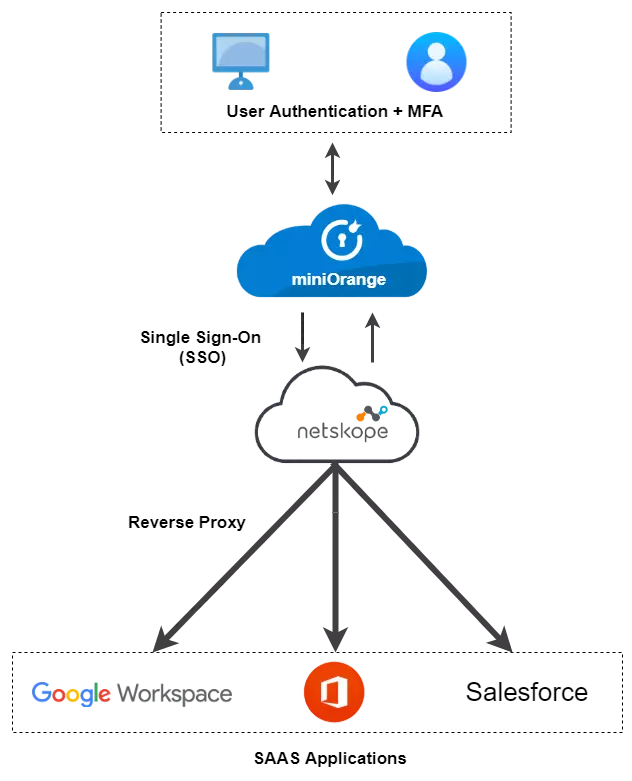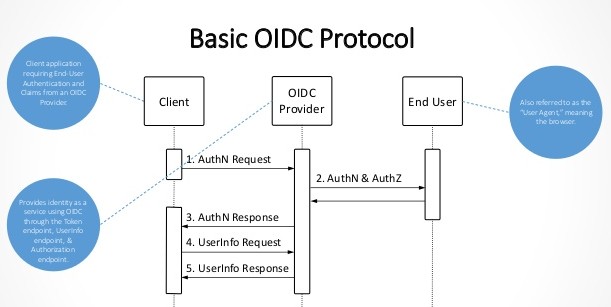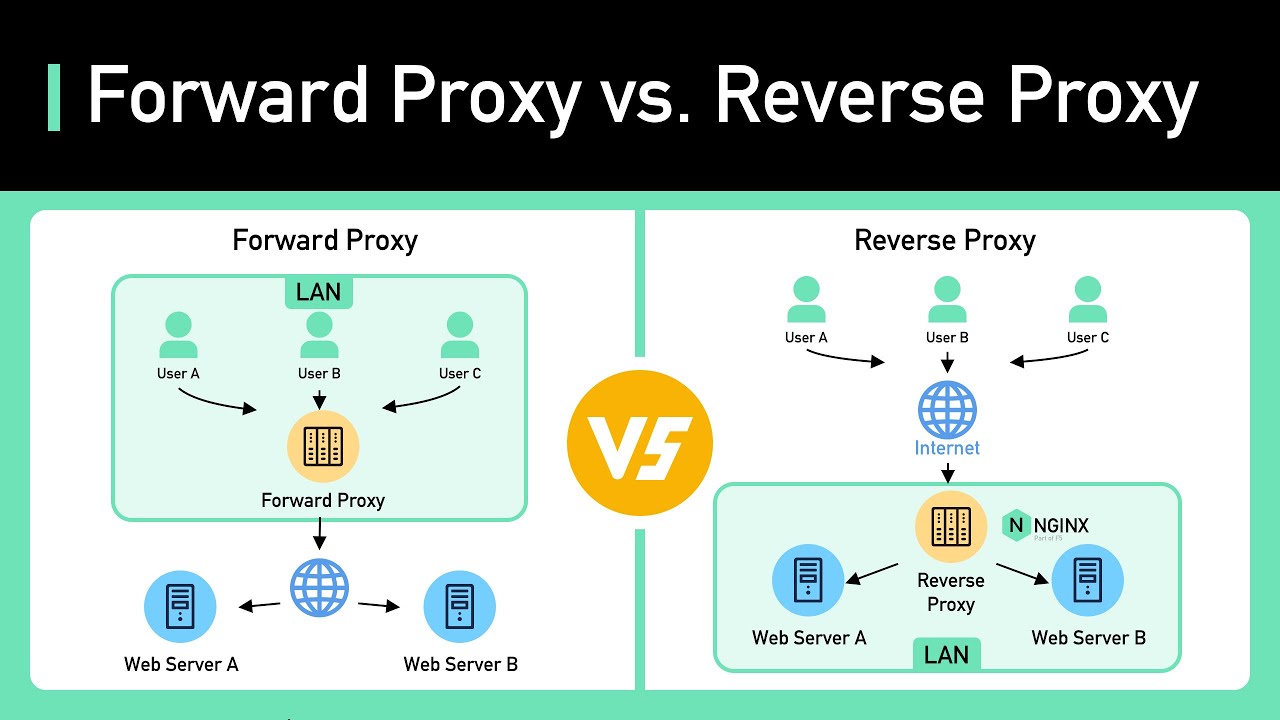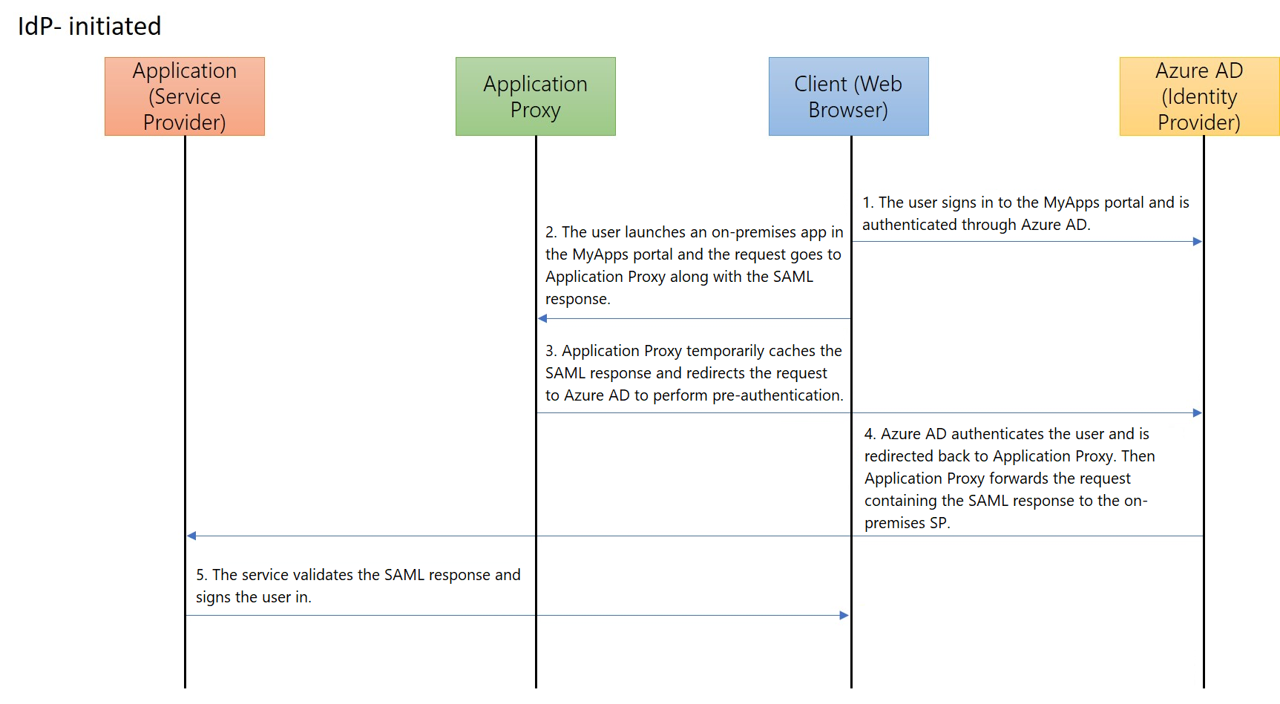
SAML single sign-on for on-premises apps with Azure Active Directory Application Proxy - Microsoft Entra | Microsoft Learn

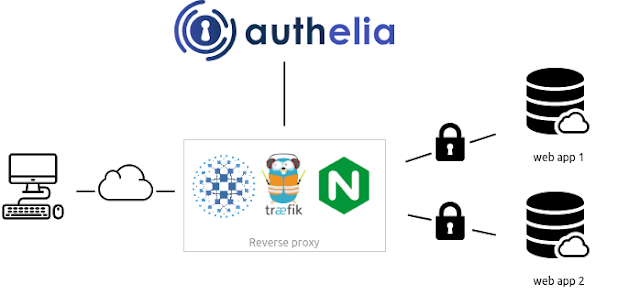
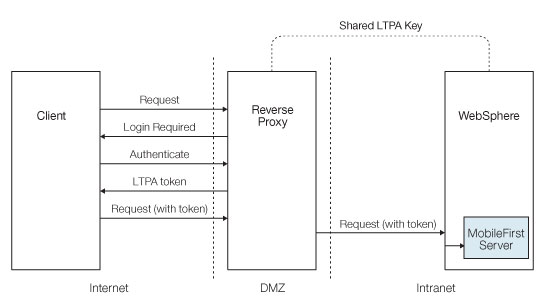
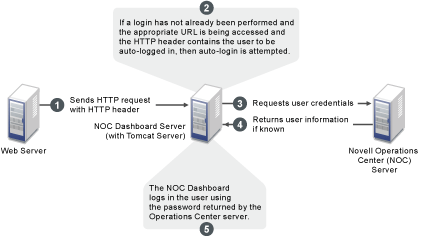
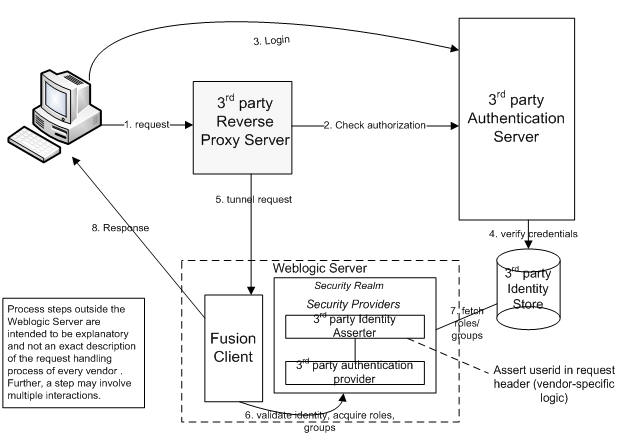
networking - Reverse proxy with login for redirecting different users to different applications - Super User
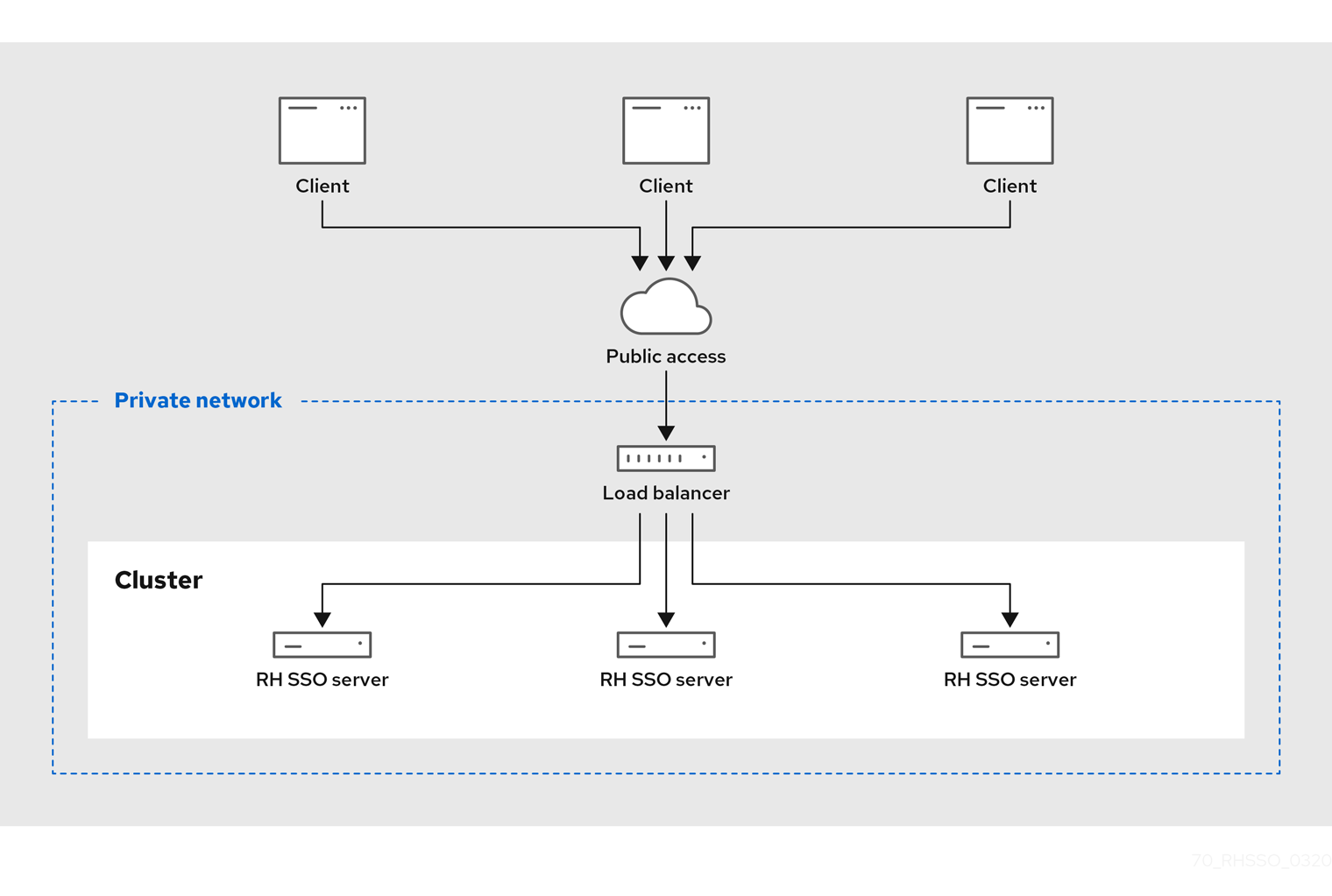
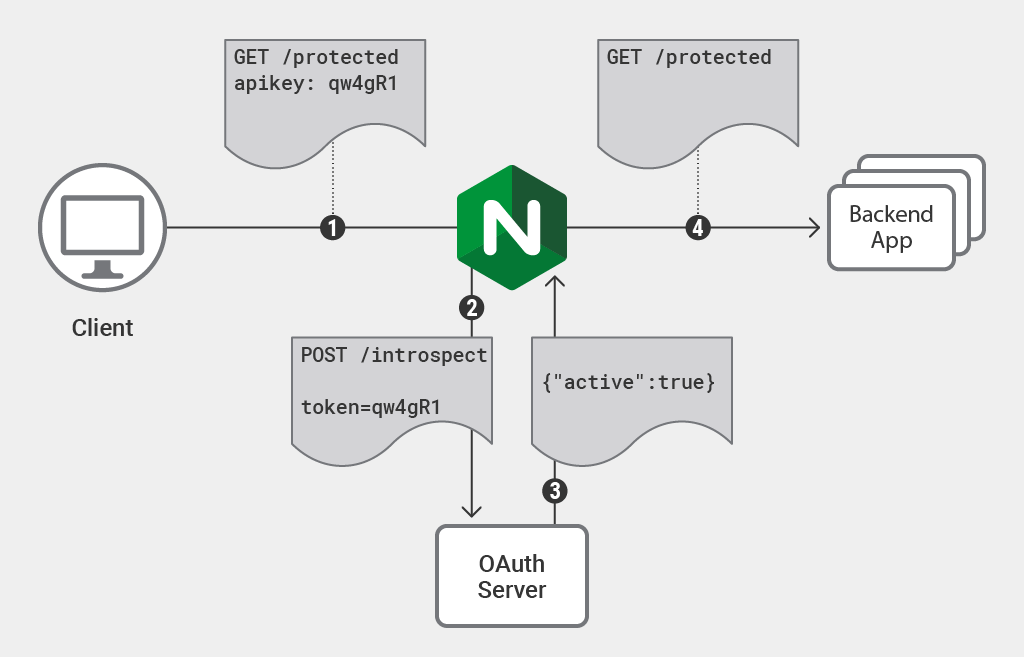
Chapter 9. Configuring Red Hat Single Sign-On to run in a cluster Red Hat Single Sign-On 7.5 | Red Hat Customer Portal